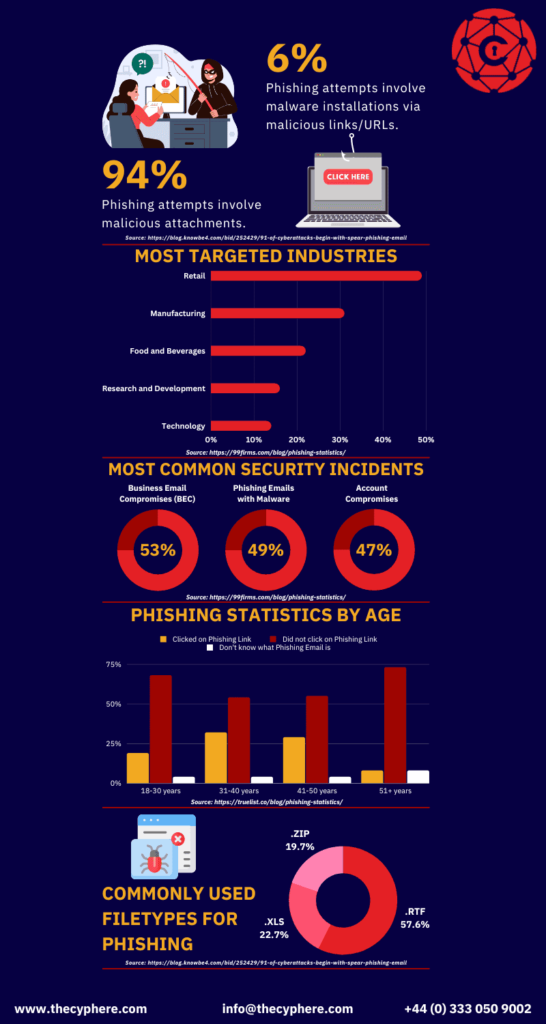
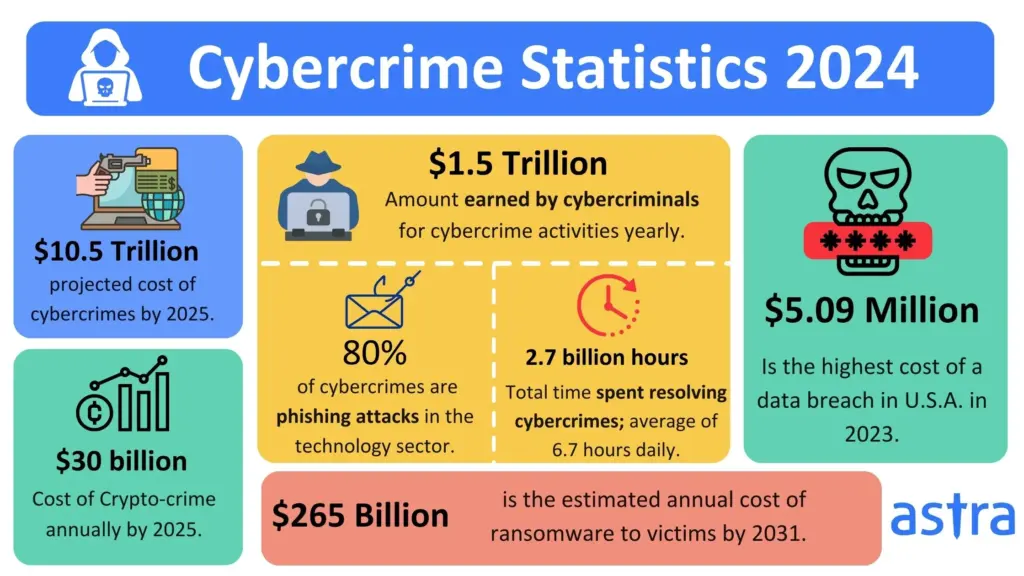
Fake RTO Traffic Challan Scam Targets WhatsApp Users: If you’ve recently received a WhatsApp message saying you’ve got an unpaid traffic fine, complete with your license plate number and a link to pay up—you’re not alone. But before you click that link, here’s a warning: you might be walking straight into a trap. Welcome to the latest in a series of digital frauds sweeping across India—the Fake RTO Traffic Challan Scam. Cybercriminals are using clever social engineering tricks to make their messages look just like official government notifications, even including real vehicle details. But the truth is, it’s not the government knocking—it’s a hacker. This article provides a comprehensive guide to this dangerous scam, real-world examples, expert advice, and a clear action plan to keep yourself and your data safe.
Fake RTO Traffic Challan Scam Targets WhatsApp Users
In today’s digital world, scams don’t need guns or masks. A simple message, a single tap, and your hard-earned money can be gone. The Fake RTO Challan Scam is just one flavor of many cyber scams making the rounds. But it teaches a powerful lesson: never trust a message without verifying it yourself. Keep your devices secure, your apps updated, and your gut instincts sharp. And if something feels off—it probably is.

| What You Need to Know | Details |
|---|---|
| Scam Type | Fake RTO Traffic Challan Scam |
| Platforms Used | WhatsApp, SMS, email, even Facebook messages |
| Main Targets | Android smartphone users with UPI/banking apps |
| Real Incidents | ₹34.75 lakh (Vadodara), ₹1.6 lakh (Delhi), ₹2 lakh (Mumbai) |
| Malware Used | APK files impersonating mParivahan, RTO apps |
| How the Scam Works | Social engineering, malicious downloads, OTP interception |
| Official Site to Verify Challans | https://echallan.parivahan.gov.in |
| Report Fraud | https://cybercrime.gov.in or dial 1930 |
What is the Fake RTO Traffic Challan Scam Targets WhatsApp Users Scam?
The scam starts with a seemingly harmless message that looks very official. It might come from a WhatsApp number posing as the local traffic police or RTO, and reads something like this:
“Your vehicle MH12XY1234 has an unpaid traffic fine of ₹1,000. Please pay immediately to avoid license suspension. Click here: rtoindia-challan[dot]in”
What makes this scam particularly effective is the use of actual vehicle registration details, often scraped from public databases or social media posts. This instantly convinces users that the message is legit.
But the link in the message doesn’t go to the official Parivahan site. It leads to a malicious APK file—essentially a rogue Android app that, once installed, steals your private information, intercepts OTPs, and empties your bank account within minutes.
And this isn’t some small-time scam. We’re talking millions of rupees lost in just the past few months.
Real-World Case Studies: Victims Speak Out
Vadodara: ₹34.75 Lakh in Minutes
Deepak Thakkar, a 47-year-old businessman, lost nearly ₹35 lakh after installing what he believed to be an “RTO Challan Payment App” from a WhatsApp link sent by a known contact. After granting the app permissions, it silently activated in the background and siphoned off money from multiple linked bank accounts.
He reported the crime within 4 hours, and though ₹4.9 lakh was reversed, the rest was gone—transferred to multiple mule accounts and converted into cryptocurrency to avoid tracing.
Delhi: Techie Falls for Fake mParivahan Clone
Ayush Goyal, a young techie, had no idea that the “mParivahan update” link he received was malicious. Within 30 minutes of installing the APK, ₹1.6 lakh was gone. The hackers gained access to his Paytm, PhonePe, and banking apps by intercepting OTPs and mimicking legitimate transactions.
Chennai: Dual-Phase Scam Exposed
In Tamil Nadu, victims of the scam were approached a second time by imposters claiming to be from a “Cyber Recovery Department.” These fake officers offered to recover their lost money—for a hefty processing fee. Victims were essentially scammed twice.
Why This Scam is So Dangerous?
This isn’t just a one-off phishing trick. This is a well-orchestrated, multi-step con using:
- Psychological pressure (fear of legal consequences)
- Technical manipulation (malicious APKs)
- Social engineering (spoofed phone numbers and links)
- Digital laundering (crypto and mule accounts)
Moreover, the malware itself is highly sophisticated. Some of these APKs:
- Install hidden background processes
- Use Telegram bots to exfiltrate data
- Auto-forward OTPs to hacker-controlled servers
- Hide from your phone’s app drawer
And with India’s growing reliance on UPI, net banking, and mobile wallets, the damage can be catastrophic in just a few taps.

How the Scam Works – Step-by-Step
Step 1: The Message
A WhatsApp/SMS alert hits your phone. It looks official and includes your vehicle number. The message often has:
- RTO or government logos
- Threats like “license suspension”
- A short link (bit.ly, goo.gl, etc.)
Step 2: The Hook
You click the link. It asks you to download a file that looks like an update or payment portal. The file ends in .apk.
Step 3: Installation and Permissions
Once you install the APK, it requests access to:
- SMS (to read OTPs)
- Contacts (to spread further)
- Accessibility (to control the device)
- Overlay (to trick you with fake login screens)
Step 4: Execution
The malware does its job—intercepts OTPs, logs keystrokes, performs transactions. Often, the app hides itself after launch.
Step 5: Financial Loss
Money vanishes via UPI, bank transfers, or digital gift card purchases. Victims are left confused, unaware of how it even happened.
What’s Being Done? Police and Government Action
- Multiple arrests have been made in Delhi, Jalandhar, and Bihar.
- The Cyber Cell of Tamil Nadu and Gujarat has issued red alerts warning citizens not to download APKs.
- The Ministry of Home Affairs has instructed state cyber teams to conduct awareness campaigns via local traffic police departments.
- CERT-IN (India’s cybersecurity agency) is tracking malware variants and advising telecom providers to block known phishing domains.
However, experts warn that law enforcement is always a step behind, due to the constantly evolving nature of cybercrime.
How to Protect Yourself: A Cyber Hygiene Checklist
- Use Only Official Apps
- mParivahan: Play Store
- Parivahan: https://echallan.parivahan.gov.in
- Never Install APKs from Links
If an app isn’t on the Play Store, don’t install it. Period. - Check URLs Carefully
Avoid clicking on shortened URLs. Always go to the official.gov.insite for challan details. - Enable Play Protect on Android
This feature scans apps and warns you before installing dangerous ones. - Revoke Excessive App Permissions
Go to Settings > Apps > App Permissions. Remove SMS, Contacts, and Storage access where not needed. - Install a Mobile Security App
Use antivirus like Bitdefender, Norton, or Kaspersky Mobile to auto-scan apps. - Educate Your Family
Scammers target elders and kids alike. Take 5 minutes to explain these dangers. - Report Immediately
If you fall victim:- Call 1930 (India’s cybercrime helpline)
- File a complaint at https://cybercrime.gov.in
Fake Invoice Scam: DGGI Detects ₹43 Crore GST Evasion
Admission Fraud Syndicate Busted, Two Arrested in Major Scam
₹92 Crore Digital Arrest Scam Exposed – Mohali Police Nab Mastermind Gang





