New Cyber Fraud Trick Lets Hackers Empty Bank Accounts: Let’s cut to the chase—there’s a new cyber fraud trick going around that’s so slick, it can drain your bank account without needing your debit card or even your OTP (one-time password). Sounds like a plot straight out of a heist movie, right? Unfortunately, it’s very real, and people around the world—including everyday Americans—are losing thousands of dollars to it every single day. This isn’t your grandma’s email scam from the 2000s. We’re talking about high-tech, AI-enhanced phishing, digital wallet abuse, and social engineering tactics so advanced, even cybersecurity pros are blinking twice. In this article, we’ll break it all down: how it works, who’s behind it, how to protect yourself, and what to do if it happens to you.
New Cyber Fraud Trick Lets Hackers Empty Bank Accounts
This cyber scam is no joke. It doesn’t need your debit card, and it doesn’t wait for you to hand over passwords—it just tricks you with one OTP and a little trust. But once you know the playbook, you can shut this scam down cold. Whether you’re 10 or 60, tech-savvy or not, remember: never click strange links, don’t enter OTPs without knowing why, and always verify who you’re talking to. We can’t stop scammers from knocking, but we can make sure they don’t get past the front door.

| Highlight | Detail |
|---|---|
| Fraud Method | Digital wallet hijack + OTP phishing + social engineering |
| US Cybercrime Losses (2025) | $18.2 billion (projected), up 9.5% from 2024 |
| Global Account Takeover (ATO) | $17 billion projected in 2025 |
| Card Hijacking in US | 115 million cards exposed in smishing attacks |
| Who’s Affected Most? | Gen Z (18-24), seniors over 60, gig workers |
| Official Reporting | FBI Internet Crime Center (IC3) |
What Is the New Scam All About?
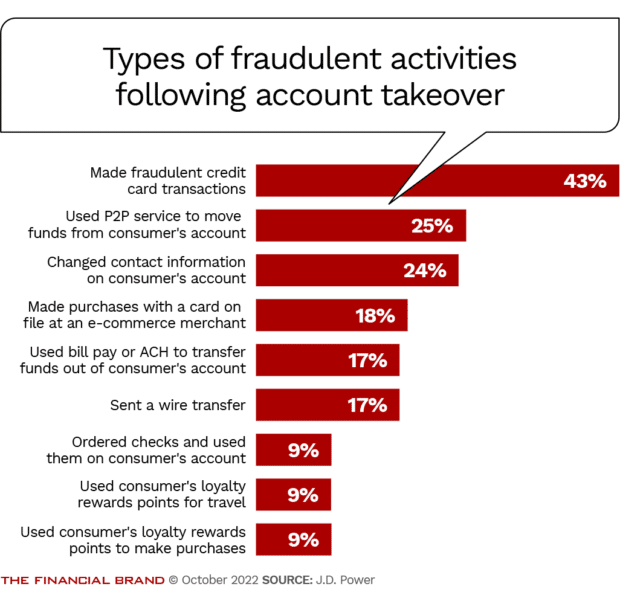
This scam bypasses the usual suspects—OTP verification, debit card usage, and even your physical phone. It all starts with a phishing or smishing message (text-based scam) that tricks you into sharing an OTP sent by your bank. That OTP? It’s not for your use—it’s being used to register your card into a scammer’s Apple Pay or Google Wallet. Once that’s done, they’re off to the races—buying stuff, paying bills, and withdrawing money using your card details on their device. And here’s the kicker: many victims don’t even realize it until days—or weeks—later, when the transactions show up on their statements.
Who’s Most at Risk?
Let’s look at who’s being targeted the most:
| Group | Why They’re Targeted |
|---|---|
| Seniors (60+) | Less familiar with digital wallets and phishing scams |
| Gen Z / Millennials | Heavy mobile usage, fast clickers on links, frequent online shopping |
| Gig Workers | Reliant on banking SMS/alerts and vulnerable to fake payout scams |
| Small Business Owners | Targeted with fake invoice and vendor payment scams |
| Remote Employees | Working across unsecured Wi-Fi or personal devices |
Real-Life Case Studies
San Diego, CA – Digital Wallet Double Tap
In July 2025, a freelance designer received a “Bank KYC Verification” text. Thinking it was legit, she entered an OTP she got via SMS. Within 20 minutes, $2,400 was charged to her card via Apple Pay purchases—on an iPhone she didn’t own.
Mumbai, India – Call Merge Scam
A retired professor was duped into merging a call between a fraudster and his bank. Thinking it was a routine verification, he shared an OTP aloud. That OTP was used to link his card to a scammer’s Google Pay, draining over ₹95,000 (~$1,100 USD).
How the New Cyber Fraud Trick Lets Hackers Empty Bank Accounts Works: Step by Step
Step 1: The Bait
You receive a text like:
“URGENT: Your bank account will be frozen. Click here to verify now!”
Or something like:
“Confirm your recent transaction or risk account suspension.”
Step 2: Fake Site or OTP Prompt
The link opens a site mimicking your bank. You’re asked for your card details, phone number, or an OTP for “security reasons.”
Step 3: Digital Wallet Enrollment
The scammer initiates a request to add your card to their Apple or Google Wallet. You receive a legitimate OTP from your bank—and you unwittingly enter it into their fake form.
Step 4: The Spend
Once your card is added to their wallet, they start shopping, sending money, or withdrawing from ATMs that accept contactless payments.
Inside the Hacker’s Toolbox
This new breed of scam relies on a growing toolkit of digital deception:
- Smishing Bots: AI-powered SMS bots personalize phishing messages in seconds.
- Remote Access Trojans (RATs): Malware hidden in fake “banking” or “loan” apps that allow full control of your phone.
- Call Merging Scams: Scammers fake bank calls, ask you to merge them, and eavesdrop while you speak with real reps.
- Device Spoofing: Fraudsters mimic a real customer’s phone environment using virtual machines to bypass device-based verification.
- OTP Forwarding Apps: Malicious Android apps silently forward OTPs to remote servers.
This isn’t some back-alley hacking—it’s commercial-grade fraud-as-a-service, often available on the dark web for as little as $200.
How to Protect Yourself?
Everyday User Tips
| Do | Don’t |
|---|---|
| Use official banking apps | Click links in SMS messages |
| Enable transaction alerts | Share OTPs with anyone |
| Use app-based MFA (like Google Authenticator) | Rely solely on SMS-based OTPs |
| Set strong passcodes on wallets | Assume every notification is harmless |
| Review account statements weekly | Delay reporting unauthorized charges |
Additional step: set up biometric authentication (like fingerprint or Face ID) for all mobile wallets and bank apps.
Advanced Safety Tips for Businesses
- Implement device fingerprinting: Identify unusual devices attempting to enroll payment credentials.
- Deploy fraud analytics: Behavioral analysis can detect sudden wallet add-ons or first-time NFC transactions.
- Train staff quarterly: Conduct phishing simulations and update training modules to include mobile-first threats.
- Monitor wallet APIs: Audit logs for digital wallet enrollment can flag irregular behavior.
- Use dual-approval for fund transfers: Especially for vendor or B2B payments.
The Business Threat Landscape
Businesses are increasingly being targeted via:
- Fake vendor invoice scams: Requests to “update bank details” with OTP prompts.
- Deepfake video/audio attacks: Executives faked using AI to approve payments.
- QR code fraud: Employees are directed to scan malicious QR codes mimicking payroll or client access forms.
According to IBM’s 2025 Cost of a Data Breach Report, stolen credentials and phishing remain the top initial attack vectors. And average breach costs are now $4.45 million per incident.
Legal Landscape and Regulatory Response
Governments worldwide are catching on:
- In the U.S., the FTC and FBI are urging stronger verification methods beyond SMS OTP. The Digital Fraud Act of 2025 proposes mandatory biometric fallback authentication for wallet provisioning.
- In India, the RBI has mandated banks to alert customers about digital wallet additions in real-time, including OTP misuse tracking.
- Europe’s PSD3 regulation, expected in 2025, will make behavioral biometrics a mandatory part of multi-factor authentication for financial apps.
NC Man Sentenced to 19 Years in Prison for Running Ponzi Scheme
Vellore Woman Gets Rs 1 Crore GST Notice – Files Complaint Against Officials
Rs 200 Crore Tax Evasion Case – Coke Plant Owner From Meghalaya Arrested By DGGI








